Taming Shadow IT: An Introduction to Zscaler ZIA's Inline CASB
Taming Shadow IT: An Introduction to Zscaler ZIA's Inline CASB
A Primer on Cloud Access Security with Zscaler ZIA
In today's fast-paced digital workplace, employees are constantly seeking tools to boost productivity. This often leads them to adopt cloud applications and services without IT's knowledge or approval—a phenomenon known as "Shadow IT." While born from good intentions, Shadow IT can open gaping holes in an organization's security posture, exposing sensitive data to unnecessary risk. How can IT teams empower employees while maintaining control and visibility?
The Case of the Creative Cloud App
Meet Brenda from Marketing. Her team is under pressure to deliver a stunning new ad campaign. She discovers "PixelPerfect AI," a revolutionary, free cloud-based design tool that promises to generate amazing visuals in seconds. It's not on the company's list of approved software, but the deadline is tight, and the tool is just too good to pass up.
Brenda starts uploading marketing briefs, product roadmaps, and confidential customer personas to PixelPerfect AI. She's creating incredible content and meeting her deadlines. Unbeknownst to her, however, PixelPerfect AI has vague terms of service and questionable data privacy practices. The company's sensitive intellectual property is now stored on a third-party server, completely outside of IT's visibility and control.
Visualizing the Shadow IT Challenge
Enter Zscaler's Inline CASB
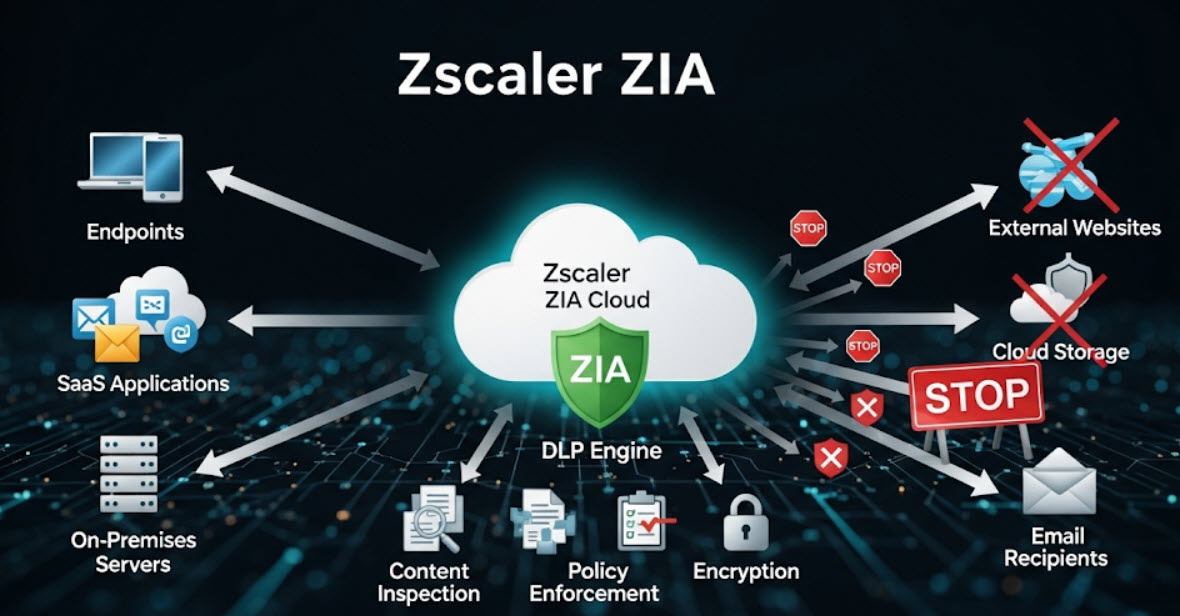
This is where Zscaler Internet Access (ZIA) and its inline Cloud Access Security Broker (CASB) capabilities transform the situation. Instead of relying on a clunky, after-the-fact detection process, Zscaler inspects all web traffic in real-time—before it even leaves your network. It acts as an intelligent checkpoint for all data heading to the cloud.
Because Zscaler sits "inline," it doesn't just see the traffic; it controls it. It can make policy decisions on the fly based on the user, the application, the location, and the type of data being sent.
When Brenda tries to upload her sensitive product roadmap to PixelPerfect AI, Zscaler's CASB engine instantly identifies the application and the action. Based on policies set by IT, it can take immediate action:
- Identify the Application: Zscaler's extensive cloud app dictionary recognizes PixelPerfect AI, even if IT has never heard of it.
- Enforce Policy: The IT admin could have a policy that blocks all "Unsanctioned AI Design Tools." Zscaler enforces this, and Brenda's upload is blocked. She receives a notification explaining why, directing her to the IT-approved design software.
- Apply Granular Controls: Alternatively, IT could be more flexible. They could set a policy that allows employees to *use* PixelPerfect AI to generate ideas but *blocks file uploads*. This allows for creative exploration while keeping corporate data safe.
- Prevent Data Loss: Zscaler's integrated Data Loss Prevention (DLP) can even inspect the content of the file itself. If it detects keywords like "confidential," "Project X Roadmap," or specific data patterns, it can block the upload automatically, regardless of the application.
From Shadow to Sanctioned: The Power of Visibility
Zscaler's inline CASB fundamentally changes the game for Shadow IT. It shifts the power back to IT, not by stifling innovation, but by providing the visibility and control needed to manage it safely. Instead of playing a constant game of cat and mouse, security teams can proactively define what's acceptable, educate users in real-time, and protect data before it ever leaves the perimeter.
By taming Shadow IT, organizations can confidently embrace the agility of the cloud, empowering employees like Brenda to do their best work without compromising on security.